Cybersecurity
Partner Content

Partner content
How businesses can safeguard themselves on the cyber frontline
Partner content
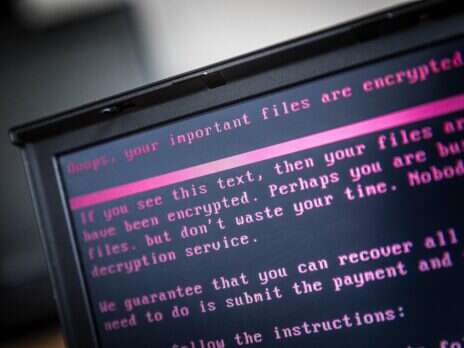
Inside ransomware’s hidden costs

Partner content